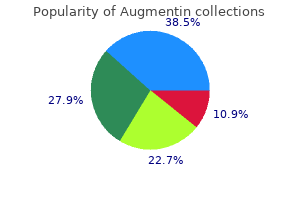
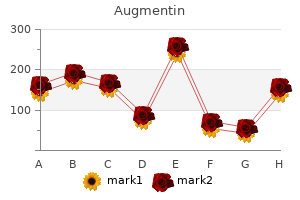
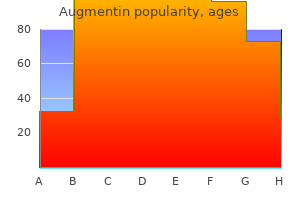
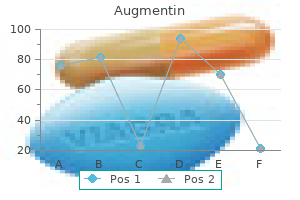
"Augmentin 375 mg generic, antibiotics for sinus infections best ones".
By: U. Kliff, M.A., M.D.
Medical Instructor, Louisiana State University School of Medicine in New Orleans
Considering the relative sizes of the sample and the population and the undecided factor infection videos order augmentin online, would you say that these polls had good accuracy? The poll was based on the responses of n = 1021 individuals non penicillin antibiotics for sinus infection purchase 625 mg augmentin mastercard, and resulted in a margin of error of approximately 3%. Find the approximate margin of error had the poll been based on a sample of size (a) n = 100, (b) n = 400, and (c) n = 1600. For example, 14% agreed that "American society is fair to everyone" when they thought the interviewer was black, but 31% agreed to this statement when posed by an interviewer that the respondent thought was white. Which type of bias does this illustrate: Sampling bias, nonresponse bias, or response bias? Suppose a survey asks, "Do you oppose the present state flag that contains the Confederate symbol, a symbol of past slavery in the South and a flag supported by extremist groups? Explain why a better way to ask this question would be, "Do you favor or oppose the current state flag containing the Confederate symbol? A group of students planning to register for a statistics course in the upcoming semester are trying to identify the instructors who receive the highest ratings on the site. The Web site ratings are unreliable because the ratings are from students who voluntarily visit the site to rate their instructors. To obtain reliable information about Professor Smith, they would need to take a simple random sample of the 78 ratings left by students on the site, and compile new overall ratings based on those in the random sample. The student polled 1500 executive recruiters, asking their opinions on the industries most likely to hire. He received back questionnaires from 97 recruiters, of whom 54 indicated that health care was the industry most likely to see job growth. Gun control More than 75% of Americans answer yes when asked, "Do you favor cracking down against illegal gun sales? Stock market associated with poor mental health An Internet survey of 545 Hong Kong residents suggested that close daily monitoring of volatile financial affairs may not be good for your mental health (J. Subjects who felt that their financial future was out of control had the poorest overall mental health, whereas those who felt in control of their financial future had the best mental health. Briefly discuss the potential problems with the sampling method used and how these problems could affect the survey results. Scientists and Army Corps of Engineers technicians used augurs, drills, and a split-spoon, which sucks up the muck of the canal bottom, to analyze what is "living" in the canal. It takes a list of the 1000 people who have subscribed to the paper the longest and sends each of them a questionnaire that asks, "Given the extremely volatile performance of the stock market as of late, are you willing to invest in stocks to save for retirement? The goal of the experiment is to investigate the association- how the treatment affects the response. An advantage of an experimental study over a nonexperimental study is that it provides stronger evidence for causation. Studies have reported that regardless of what smokers do to quit, most relapse within a year. Some scientists have suggested that smokers are less likely to relapse if they take an antidepressant regularly after they quit. How can you design an experiment to study whether antidepressants help smokers to quit? For this type of study, as in most medical experiments, it is not feasible to randomly sample the population (all smokers who would like to quit). For instance, a medical center might advertise to attract volunteers from the smokers who would like to quit. Control comparison group Suppose you have 400 volunteers who would like to quit smoking. You could have each start taking an antidepressant, and then a year from now check how many have relapsed. An experiment normally has a primary treatment of interest, such as receiving an antidepressant. But it should also have a second treatment for comparison to help you analyze the effectiveness of the primary treatment. So the volunteers should be split into two groups: One group receives the antidepressant, and the other group does not. You could give the second group a pill that looks like the antidepressant but that does not have any active ingredient-a placebo.
If the entries in this deletion buffer are headed with simple date stamps and document names infection rates for hospitals buy generic augmentin 375mg on line, navigation would be very simple and visual antibiotics loss of taste quality 625 mg augmentin. Users can then browse the buffer of deleted data at will, randomly, rather than sequentially. Finding those six missing paragraphs would be a simple, visual procedure, regardless of the number or type of complex, intervening steps she had taken. A deleted data buffer should be offered in addition to the regular, incremental, multiple Undo because it complements it. This feature would be quite useful in most programs, too, whether spreadsheet, drawing program, or invoice generator. Versioning and reversion Users occasionally want to back up long distances, but when they do, the granular actions are not terrifically important. The need for an incremental Undo remains, but discerning the individual components of more than the last few operations is overkill in most cases. Because versioning involves the entire document, it is typically implemented by direct use of the file system. The biggest difference between versioning and other Undo systems is that the user must explicitly request the version - recording a copy or snapshot of the document. If he later decides that his changes were undesirable, he can return to the saved copy - a previous version of the document. Chapter 16: Understanding Undo 347 Many tools exist to support the milestoning concept in source code, but this concept is just emerging in the world outside of programming. Critical to the effectiveness of a versioning facility is the behavior of the "revert" command. It should provide a list of the available saved versions of the document in question, along with some information about each one, such as the time and day it was recorded, the name of the person who recorded it, the size, and some optional user-entered notes. A user should be able to understand the differences among versions and ultimately choose to revert to any one of these versions, in which case, the current state of the document should be saved as another version that can be reverted to . It creates a new version every time a user saves changes to the document, and allows users to compare the different versions. This can be quite useful as it allows collaboration to take its course without worry that valuable work will be overwritten. Anything that has been entered becomes unmodifiable, although new data can be added. Existing paragraphs are untouchable, but new ones can be added between older ones. All marks made up to that point are now permanent, yet new marks can be made at will. Images already placed on the screen are locked down and cannot be changed, but new images can be freely superimposed on the older ones. Undo-Proof Operations Some operations simply cannot be undone because they involve some action that triggers a device not under the direct control of the program. Many operations, however, masquerade as Undo-proof, but they are really easily reversible. For example, when you save a document for the first time in most programs, you can choose a name for the file. Sure, you can Save As under another name, but that just makes another file under the new name, leaving the old file untouched under the old name. Examples here include records of financial transactions, or entries in a medical record. Things start out all right: You start up the word processor and type a couple sentences. But when you click the Close button, up pops a dialog box asking "Do you want to save changes? In our experience, people find computer file systems - the facilities that store application and data files on disk - very difficult to use and understand.
Where the sovereign can dig a hole and pour a concrete foundation for itself antibiotic for uti pseudomonas effective augmentin 625mg, the transient application is just on a weekend campout antibiotics for uti intravenous generic augmentin 625mg free shipping. In cases when the entire computer system is fulfilling a transient role in the real world of atoms, it is not necessarily appropriate to minimize the use of pixels and visual attention. Examples of this include process monitors in a fabrication environment, or digital imaging systems in an operating theatre. Here, the entire computer screen is referred to in a transient manner, while the user is engaged in a sovereign mechanical activity. In these cases, it is critical for information to be obvious and easily understood from across the room, which clearly requires a bolder use of color and a more generous allotment of real estate (see Figure 9-3). The use of rich dimensional rendering gives them an appropriate amount of visual gravity. Bright and clear Whereas a transient application must conserve the total amount of screen real estate it consumes, the controls on its surface can be proportionally larger than those on a sovereign application. On the contrary, bolder graphics help the user to orient himself more quickly when the application pops up. The user may only see the application once a month and will likely forget the meanings and implications of the choices presented. Likewise, nothing should be abbreviated on a transient application, and feedback should be direct and explicit to avoid confusion. For example, a user should be easily able to understand that the printer is busy, or that a piece of recently recorded audio is five seconds long. Direct manipulation can also be effective, but anything directly manipulable must be discoverable and big enough to interact with easily. You should also provide keyboard shortcuts, but they must be simple, and all important functions should also be visible on the interface. Of course, there are some rare exceptions to the monothematic nature of transient applications. If a transient application performs more than just a single function, the interface should communicate this visually and unambiguously and provide immediate access to all functions without the addition of windows or dialogs. One such application is the Art Directors Toolkit by Code Line Communications, which performs a number of different calculator-like functions useful to users of graphic design applications (see Figure 9-4). Keep in mind that a transient application will likely be called upon to assist in the management of some aspect of a sovereign application (as in the Art Directors Toolkit in Figure 9-4). This means that the transient application, as it is positioned on top of the sovereign, may obscure the very information that it is chartered to work on. This implies that the transient application must be movable, which means it must have a title bar or other obvious affordance for dragging. Figure 9-4 Art Directors Toolkit by Code Line Communications is another example of a transient application. It provides a number of discrete functions such as calculating dimensions of a layout grid. These functions are designed to support the use of a sovereign layout application such as Adobe InDesign. While this application provides a number of different functions, they are organized into tabs and are all directly accessible at all times. It is completely unreasonable to force the user to add nonproductive window-management tasks to this interaction. Remember user choices the most appropriate way to help users with both transient and sovereign apps is to give the applications a memory. If a transient application remembers where it was the last time it was used, the chances are excellent that the same size and placement will be appropriate next time, too. Whatever shape and position a user morphed the application into is the shape and position the application should reappear in when it is next summoned. You can see that all the preceding guidelines for transient applications apply equally well to the design of dialog boxes (for more on dialog boxes, see Chapters 24 and 25). Daemonic posture Programs that do not normally interact with the user are daemonic posture applications. These applications serve quietly and invisibly in the background, performing possibly vital tasks without the need for human intervention. As you might expect, any discussion of the user interface of daemonic applications is necessarily short.
Syndromes
- Margarines, shortening, and cooking oils that have more than 2 grams of saturated fat per tablespoon.
- Long-term, daily sun exposure (such as in people who work outside)
- Lactate dehydrogenase (LDH) level
- Some steam iron cleaners
- Intestinal disease
- Blood collection in the chest (hemothorax)
- Sexual partners of those who engage in high-risk activities (such as injection drug use or anal sex)
- Feeding difficulties
List of Rules In this table antibiotics groups generic 625mg augmentin with amex, you can view the information of the entries and edit them by the Action buttons virus envelope generic augmentin 1000 mg with amex. Control When: Default Limit Limited Bandwidth: Default Limit applies only for users that are not constrained by Bandwidth Control Rules. If there are data flowing into the Router from interface A and out from interface B while the downstream bandwidth of A is different from the upstream bandwidth of B, then the smaller one should be considered as the effective bandwidth, and vise versa. Choose the menu AdvancedTraffic ControlBandwidth Control to load the following page. Figure 4-28 Bandwidth Control the following items are displayed on this screen: -58- Bandwidth Control Rule Direction: Select the data stream direction for the entry. Individual: the bandwidth of each user equals to the current bandwidth of this entry. Guaranteed Bandwidth (Up): Limited Bandwidth (Up): Guaranteed Bandwidth (Down): Limited Bandwidth (Down): Effective Time: Description: Status: Specify the time for the entry to take effect. The first entry in Figure 4-28 indicates: the users within group "sales" share the bandwidth and the Downstream/Upstream Guaranteed Bandwidth is 5000kbps, while the Downstream/Upstream Limited bandwidth is 10000kbps. It is impossible to satisfy all the guaranteed bandwidth if the total guaranteed bandwidth specified by all Bandwidth Control rules for certain interface exceeds the physical bandwidth of this interface. Figure 4-29 Session Limit the following items are displayed on this screen: General Enable Limit: Session Check here to enable Session Limit, otherwise all the Session Limit entries will be disabled. List of Session Limit You can view the information of the entries and edit them by the Action buttons. The first entry in Figure 4-29 indicates: the amount of maximum sessions for the hosts within group1 is 100 and this entry is enabled. Figure 4-30 Session List In this table, you can view the session limit information of users configured with Session Limit. Figure 4-32 Policy Routing -62- the following items are displayed on this screen: General Protocol: Select the protocol for the entry in the drop-down list. If the protocol you want to set is not in the list, you can add it to the list on 4. List of Rules You can view the information of the entries and edit them by the Action buttons. This entry is activated d and will take effect at 8 am to 10 pm from Monday to Friday. Backup Effective Time: Specify the backup effective time if Timing Mode has been selected. When the start time you enter is not earlier than the end time, the default effective time is from the start time of the day to the end time of the next day. List of Protocol You can view the information of the entries and edit them by the Action buttons. Static Route is a kind of special routing configured by the administrator, which is simple, efficient, and reliable. Commonly used in small-sized network with fixed topology, Static Route does not change along with the network topology automatically. The administrator should modify the static route information manually as long as the network topology or link status is changed. Figure 4-35 Static Route the following items are displayed on this screen: Static Route Destination: Subnet Mask: Next Hop: Interface: Enter the destination host the route leads to . Then click the <Scan> button, the Router will scan all the active hosts within the scanning range and display the result in the list. To bind the entries in the list, check these entries and click the <Import> button, then the settings will take effect if the entries do not conflict with the existed entries. It is recommended to check all the Flood Defense options and specify the corresponding thresholds. Application Example: Network Requirements: Prevent the local hosts from accessing Internet website Figure 4-42 Web Filtering Check the box before Enable Web Filtering and select the web components to be filtered.
Buy generic augmentin 375mg on-line. SKINS Women's A400 Compression Long Tights | SwimOutlet.com.